We are Voraltex
We remain true to the same principles on which our company was founded over a hundred years ago: providing superior service to our clients, putting safety first, creating opportunities for our people!
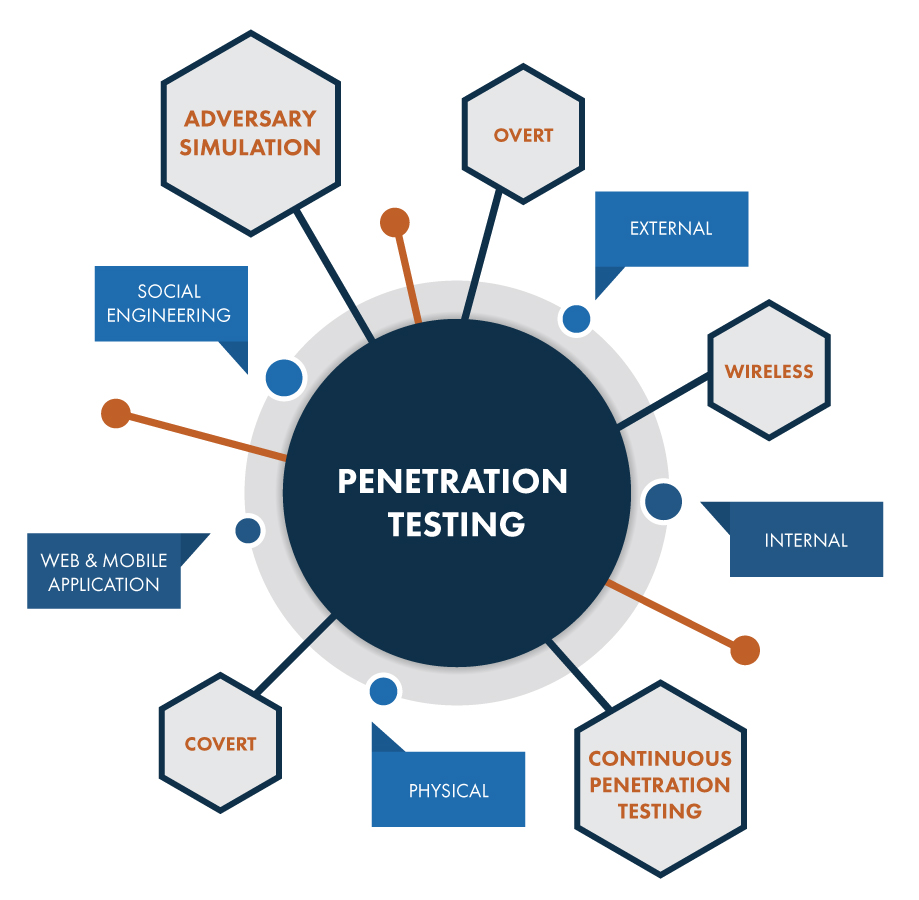
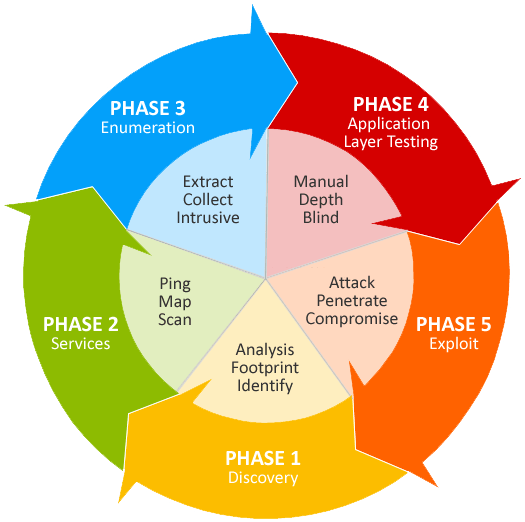
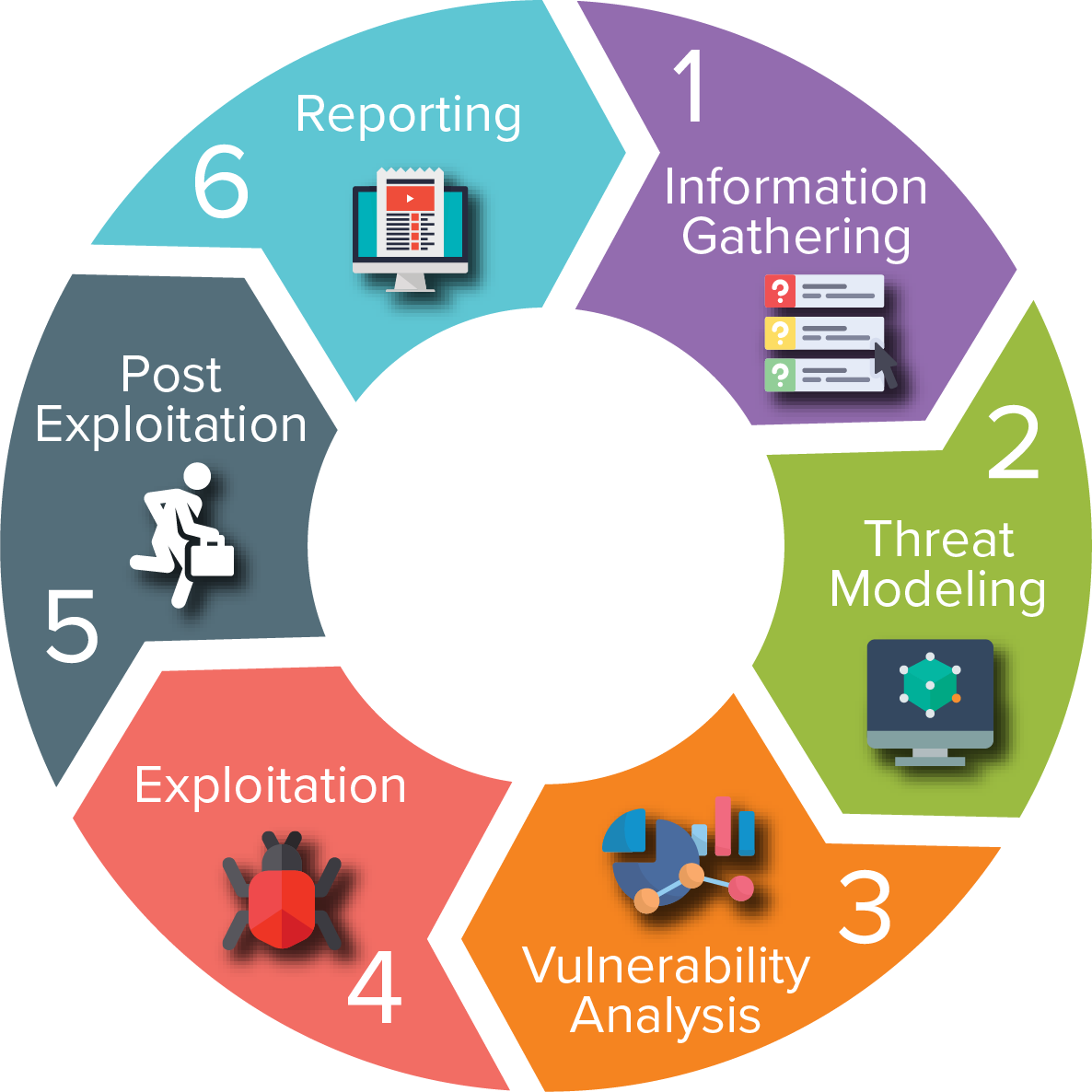
Penetration Testing
Voraltex’s expert penetration testers conduct comprehensive in-depth assessments of IT systems, with the owner’s permission, revealing hidden secrets in the same way as real attackers do. We help to transform the technical findings into immediately actionable remediation steps – aiming to protect your needs and hard-won reputation.
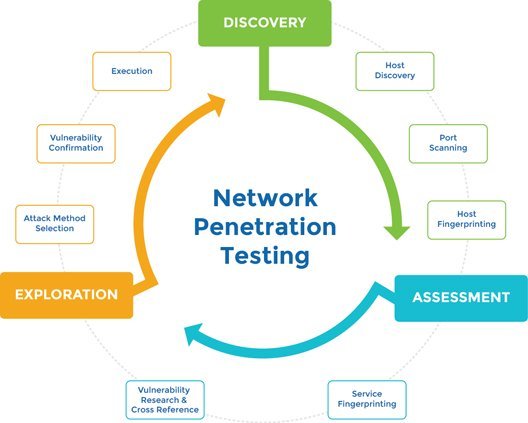
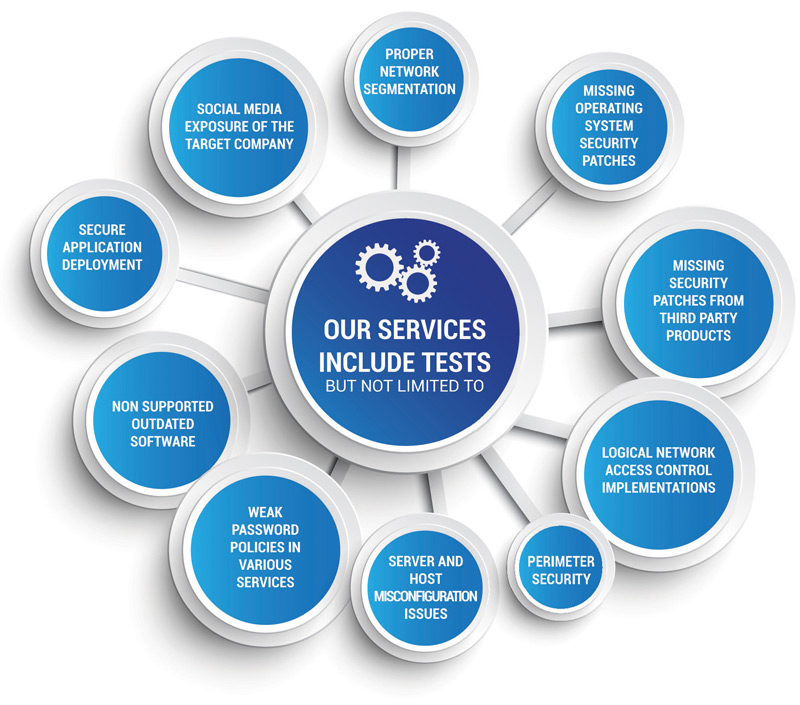
Our penetration testing service involves an active analysis of the asset for any potential security vulnerability. This could result from poor or improper configuration, both known and unknown hardware or software flaws, and operational weaknesses in process or technical countermeasures. The analysis is carried out to simulate real-life cyber attacks from the position of a potential attacker and can involve active exploitation of security vulnerabilities. We will work closely with you to help identify and eliminate areas of potential risk. Any security issues that are found will be presented to your organisation, together with an assessment of their impact, and often with a proposal for mitigation or a technical solution
Wireless Assessments
Wireless vulnerability testing is important to any organisation concerned about their network security. It should be thought of as an extension to an organisation’s overall network security and part of any infrastructure penetration test or vulnerability testing exercise. Our team has built up strong experience in testing wireless security over the years by understanding how various wireless networks are architected and implemented.
This is done by either using the wireless security standards or leveraging wireless security mechanisms, provided by reputable vendors to mitigate risk. We undertake wireless security sweeps throughout the testing process. In additon, we can work from both external and internal points of a company and have the latest tools to facilitate our expertise.
Service Brochure

At TheBuilt we are committed to green building and sustainability in our offices as well as on our job sites. We believe green buildings are not only good for the environment, they also provide immediate and long-term economic benefits.
Database Assessment
Database security is a specialist topic which overlaps with computer security, information security and risk management. The database security assessment we provide is about checking various information security controls aimed to protect your database against compromises of their confidentiality, integrity and availability. The set of our tests checks various types or categories of controls, such as technical, procedural and physical. We will analyse your database (such as: MS SQL, Oracle, MySQL, etc.) and check its configuration, security features, access rights, system and object privileges and many more.
We connect expertise across services, markets, and geographies to deliver transformative outcomes. Worldwide, we design, build, finance, operate and manage projects and programs that unlock opportunities.
Embedded in our culture of hard work, honesty, and getting the well done job, our history tells not only much about our past but also it does our present.е Our record of succeeding, surviving, and striving to be the best is central to our reputation today.
Managed Vulnerability Scanning
Regular penetration testing reports showing either complete system status or changes since your last vulnerability scan, are provided by our dedicated security experts. We reduce your administrative and maintenance burdens so you can better focus on protecting your assets and, most importantly, reducing business risk. Managed vulnerability scanning is vital to identify and remediate vulnerabilities within your IT environment, before hackers can gain exploit them. And overall can reduce and manage risk on an on-going basis to prevent cyber-attacks on external-facing networks. However it is recommended to carry out vulnerability scanning alongside regular penetration testing, to ensure all bases are covered.
Do you have any
questions?
Contact us at Voraltex office nearest to you or submit a business inquiry onlineMobile & Device Security
With the increase in mobile devices being used in everyday life as well as in corporate environments, there is a heightened demand for the security of mobile applications. Voraltex delivers comprehensive mobile application security assessments for iOS and Android environments.
These operating systems on tablets and smart phones cover the vast majority of the mobile market share – giving peace of mind to you and your customers by ensuring that your applications are secure.
Social Engineering
Social engineering is the process of finding personally identifiable or sensitive information in order to deceive or manipulate a person or organisation into performing an action which breaches physical or information security.
We will check whether your organisation is resistant to a variety of simulated social engineering attacks, conducted over the Internet, over the phone or physically at your premises. We understand that information for organisations is a key asset and protecting that information is vital. Organisations can spend large amounts of money protecting the IT infrastructure on which the information is stored and processed, but sometimes overlook the weakest point of the system – the users.